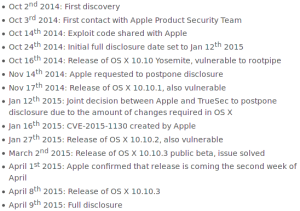
Apple has released an update and a security notice about a vulnerability in their interprocess communication (XPC) entitlements. This vulnerability allowed for users to gain root access from an unprivileged user. The vulnerability involved tricking the writeconfig XPC service to generate a setuid file owned by root with read and write privileges for all.

Attackers can easily use this file to privilege escalate to root since if it is executed it will run as root but the dangerous part is that anyone can modify the contents of a file. An attacker could replace the contents of that file with a shell which would give them a root shell. In order to trick the writeconfig XPC, the researcher had to send a nil to “authenticateUsingAuthorization” in order to get the authorization to use writeconfig.
This allowed them to authenticate and generate the setuid file.
October 14nd 2014 is when the vulnerability was originally shared with Apple, and a patch was released April 8th 2015. This means that it took nearly 6 months for Apple to fix this bug, which is nearly double the time that Google gives companies to fix the issue, I guess it’s a good thing Google didn’t find it first.
Edward Mead (exm6939)
Image Source & Link to full article: https://truesecdev.wordpress.com/2015/04/09/hidden-backdoor-api-to-root-privileges-in-apple-os-x/
Apple Update / Notice: https://support.apple.com/en-us/HT204659
You must be logged in to post a comment.